Information Security Writing Specialists
Information Security Plans, Policies and Procedures–A Proactive Approach
You will never see the hooded hacker coming, nor can you anticipate the cost of ransomware. Information security measures can be breached by skilled cybercriminals who can take down entire systems in an instant. But you will feel the impact of the cost of a massive breach, lost clients, and a hit to your reputation. Patient privacy may be destroyed, endangering their care. An extreme case was the publication of patient records on the Internet by a transcription company. Cyberthreats are real and ignoring them is a risk that most companies cannot take.
Effective risk management of information security is no longer the preserve of major corporations. Exposure to cyberthreats is now universal and affects businesses of all sizes. Written information security policies and procedures are critical. Incident response planning, business continuity, is an essential part of information security risk management.
It would be disingenuous to say that adequately documenting your information security situation will ensure adequate risk management, but that isn’t the case. You may still be hacked or become a ransomware victim. What it can do, however, is ensure that to the greatest extent possible your organization is following best practices security policies to avoid such incidents.
Southwest Business Services has provided remote technical writing services for more than 30 years. We create custom State- and NIST-compliant Information Security documentation for business of all sizes. We have long been committed to providing highly professional, due-diligent technical writing services–at an affordable price.
Is Anyone Exempt?

According to the DBIR Verizon 2024 Data Report: Roughly one-third of all breaches involved Ransomware or some other Extortion technique. Pure Extortion attacks have risen over the past year and are now a component of 9% of all breaches. The shift of traditional ransomware actors toward these newer techniques resulted in a bit of a decline in Ransomware to 23%. However, when combined, given that they share threat actors, they represent a strong growth to 32% of breaches.
We have revised our calculation of the involvement of the human element to exclude malicious Privilege Misuse in an effort to provide a clearer metric of what security awareness can affect. For this year’s dataset, the human element was a component of 68% of breaches, roughly the same as the previous period described in the 2023 DBIR.
In this issue, we are introducing an expanded concept of a breach involving a third party that includes partner infrastructure being affected and direct or indirect software supply chain issues—including when an organization is affected by vulnerabilities in third party software. In short, those are breaches an organization could potentially mitigate or prevent by trying to select vendors with better security track records. We see this figure at 15% this year, a 68% increase from the previous year, mostly fueled by the use of zero-day exploits for Ransomware and Extortion attacks.
Our dataset saw a growth of breaches involving Errors, now at 28%, as we broadened our contributor base to include several new mandatory breach notification entities. This validates our suspicion that errors are more prevalent than media or traditional incident response-driven bias would lead us to believe. Read more here..
Information security Technical Writing Servces
INFOSEC Writing
- Policies
- Standard Operating Procedures
- Manuals and Handbooks
- Onboarding and Training Materials
- Participate in Strategy Development
- Audit Preparation
- INFOSEC Technical Writing
- Regulatory Compliance
Risk Management
- Risk Assessments and Gap Analyses
- Written Information Security Plans
- Disaster Recovery Plan
- ISO 27001
- NIST 800-53
- NIST CSF, ISO 27002, FFIEC, HIPAA-HiTECH
- Incident Response Documentation
- Compliance Documentation

Incident Response
Our incident response plans are documented, written plans with six distinct phases that helps the staff recognize and deal with a cybersecurity incident like a data breach or cyber attack. Every plan has controls built into it to facilitate regular updates and training. These plans include a set of protocols that identify, detect, and address disruptive events such as data breaches.
Each staff member is aware of their responsibility and each individual has a policy and procedure to follow in addition to the Company policy.
And, of course, they include the requisite WISP.
Written Information Security Plans
The NIST Cybersecurity Framework (CSF)-based Written Information Security Program (WISP) is a set of cybersecurity policies and standards that are suited for smaller organizations or those governed by NIST 800-53.
While WISPs are often thought to be the preserve of larger businesses, we include businesses with fewer than 500 employees that also require the protection afforded by a WISP.
Whether they are included as part of the WISP or simply referred to as part of an abbreviated description, we provide complete policies and procedures referenced in the WISP.
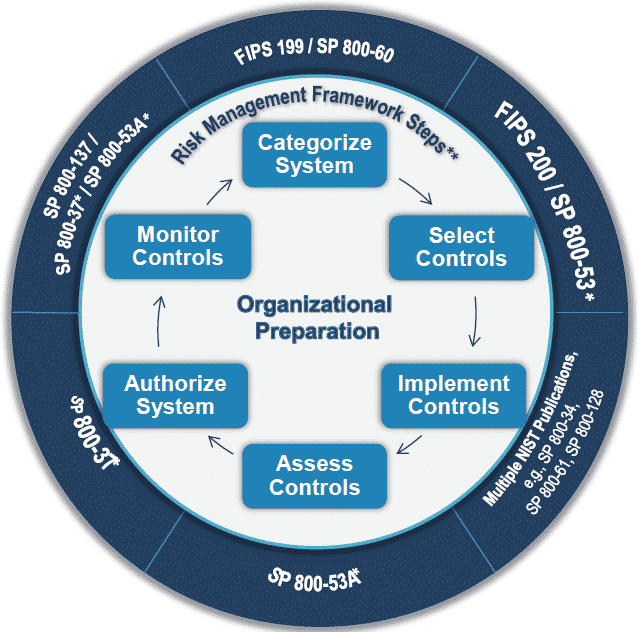
The NIST Risk Framework
is a set of guidelines and best practices to help organizations build and improve their cybersecurity posture. The framework puts forth a set of recommendations and standards that enable organizations to be better prepared in identifying and detecting cyber-attacks, and also provides guidelines on how to respond, prevent, and recover from cyber incidents.
Drafted by the National Institute of Standards and Technology (NIST), this cybersecurity framework addresses the lack of standards when it comes tocybersecurity and provides a uniform set of rules, guidelines, and standards for organizations to use across industries.
NIST Special Publication 800-53 Revision 5 Full Text
This free download is the full text of the NIST Revision 5, September 2020. This publication provides a catalog of security and privacy controls for information systems and organizations to protect organizational operations and assets, individuals, other organizations, and the Nation from a diverse set of threats and risks, including hostile attacks, human errors, natural disasters, structural failures, foreign intelligence entities, and privacy risks.
Why Work With Us?
We are creative, believers in critical thought. Our layouts are sophisticated and appropriate, effective. Our work is informative and engaging. Let our technical writing services save you time, money, revisions and failed presentations.